-
Privacy and Data Protection
Our digital risk team is made up of a combination of subject matter experts and technical specialists who can help your business comply with the GDPR.
-
Governance, Risk and Compliance (GRC)
While business goals and strategies evolve, our services support you wherever you are in your business cycle. The digital economy is simultaneously increasing the magnitude of new business opportunities while increasing the difficulty of getting it right.
-
ISO 27001 and ISO 27701
Grant Thornton’s ISO 27001 and ISO 27701 specialists will arrange and oversee the formal audit process.
-
SOC 1,2,3
As a service organization there are many ways to provide assurance to your customers and in turn other stakeholders over your control environment. One of the most effective and cost-efficient ways is to issue a Service Organization Control (SOC) Report.
-
Incident Response
Grant Thornton’s Cyber Incident Response Team can support your business in the event of a cyberattack or data loss event. We work alongside your existing IT and Legal teams to provide a co-ordinated, timely and efficient investigation and remediation.
-
Hacking Services
At Grant Thornton, our cyber security experts can develop a bespoke penetration testing plan to meet your business needs and unique IT environment. We can undertake the full suite of testing or conduct individual assessments, as required.
-
Cyber Health Check
Approximately 54% of organizations report that they have experienced at least one cyber-attack during the past year. Grant Thornton’s cyber health check provides you with an objective, jargon-free assessment of your current cyber security, drawing on both qualitative and quantitative elements.
-
Dark Web Threat Intelligence
We use a variety of dark and deep web monitoring tools that continuously scans illegal sites to discover any mention of your data, ranging from breached security credentials such as usernames and passwords to leaked confidential documents of your company.
-
Digital forensics and electronic discovery
We offer a full suite of digital forensics and data acquisition services in investigations related to cybercrime, disputes, fraud and regulatory investigations.
-
Insolvency
If you're facing a time of personal or corporate financial crisis you need advice from someone who listens, who understands your specific issues and deals with them in a supportive and sensitive manner.
-
Crisis stabilisation and turnaround
In periods of financial distress, management teams often face considerable challenges, with many directors having little or no experience of similar conditions.
-
Operational and financial restructuring
Companies challenged by underperformance often need support in identifying options for financial or operational restructuring. Tapping this type of advice helps them create a stable platform for business turnaround.
-
Accelerated M & A
Even fundamentally sound businesses run into difficulties. Cash flow can come under pressure from the loss of a big client, or a dip in performance can threaten a breach of banking covenants if there is insufficient headroom.
-
People Services
Our HR Outsourcing solutions are designed to provide you with the flexibility and expertise needed to manage your people effectively and efficiently.
-
Relocation made easy!
We bring to the table our in-depth understanding of Cyprus immigration legislation and policies, coupled with long experience supporting corporate clients relocating non-EU staff to Cyprus, as well as entrepreneurs and executives moving with their families.
-
Family Office Services
In an era of rising digital threats, protecting the sensitive information and assets of high-net-worth families is paramount. In collaboration with our dedicated strong Cybersecurity and Data Protection team, we can help ensure the data security and privacy of your Family Office (employees and c-suite), family members and any staff supporting them, and also trusted associates.
-
Client Vacancies
As part of our People, Relocation and Family Office Services, we support our clients in finding talent to meet their unique needs. Here, you’ll find open positions available within our clients’ businesses across a variety of industries. Browse the opportunities below to see how you can become part of their teams!
-
Indirect Tax
Our experienced VAT specialists are available to assist companies and entrepreneurs of all industries and sizes in meeting their obligations.
-
Direct Tax
We can help you ensure a bespoke balance between tax compliance and effective tax planning for your special circumstances.
-
Ημερίδα Γνωριμίας με την Grant Thornton Κύπρου
Σας προσκαλούμε σε μια μοναδική ευκαιρία να γνωρίσετε την Grant Thornton Κύπρου! Την Τρίτη, 5 Νοεμβρίου 2024, θα έχετε τη δυνατότητα να συναντήσετε την ομάδα μας, να ενημερωθείτε για επαγγελματικές ευκαιρίες και να εξερευνήσετε πιστοποιήσεις όπως ACCA.
-
Life at Grant Thornton
At Grant Thornton Cyprus, we are taking a holistic approach and reimagining the way we work, continually assessing it and making necessary changes to better support our people.
-
In the community
Unlocking the potential for growth in our local communities.
-
Diversity and inclusion
Diversity helps us meet the demands of a changing world. We value the fact that our people come from all walks of life and that this diversity of experience and perspective makes our organisation stronger as a result.
-
Global talent mobility
One of the biggest attractions of a career with Grant Thornton Cyprus is the opportunity to work on cross-border projects all over the world.
-
Learning and development
At Grant Thornton we believe learning and development opportunities allow you to perform at your best every day.
-
Our values
We are a values-driven organisation and we have more than 56,000 people in over 140 countries who are passionately committed to these values.
Sophisticated cyber attacks pose a serious threat for organisations today. Many businesses, have had their data compromised due to insecure systems and a lack of safeguards. Data breaches can have serious financial and legal implications, as well as lasting reputational damage.
Most modern business models are built around online processes and electronic communications. While this streamlines operations and improves business agility, it also creates a series of cyber vulnerabilities. If exploited, these vulnerabilities can lead to data breaches and significant business disruption.
What are the implications?
Data breaches can leak commercially sensitive information and staff or customer details. This can lead to customer distress, loss of assets, long term reputational damage, and regulatory fines or censure. Business disruption can grind your business to a halt leading to reputational damage and lost opportunities.
What are the key considerations?
Cyber threats refer to a potential malicious attempt to damage or disrupt a business computer network or system. They evolve on a daily basis and organisations need to continually re-assess the risks and associated controls. Businesses should continuously assess their exposure to both internal and external attacks, weighing them up against client information, networks and current systems. An effective cyber security framework should incorporate preventative, detective and corrective solutions. To test the robustness of the cyber security defences, organisations should undertake regular vulnerability assessments and penetration tests:
- Vulnerability assessments explore and identify weaknesses in cyber security controls. Identification is the first step in mitigating risk and creating a secure network. They can also help to validate the design of cyber security controls.
- Penetration tests form the next step in reviewing the robustness of cyber security defences. These tests exploit the identified vulnerabilities, with the aim of breaching an organisation’s security perimeter – thus testing how effectively security controls are operating.
What is a penetration test?
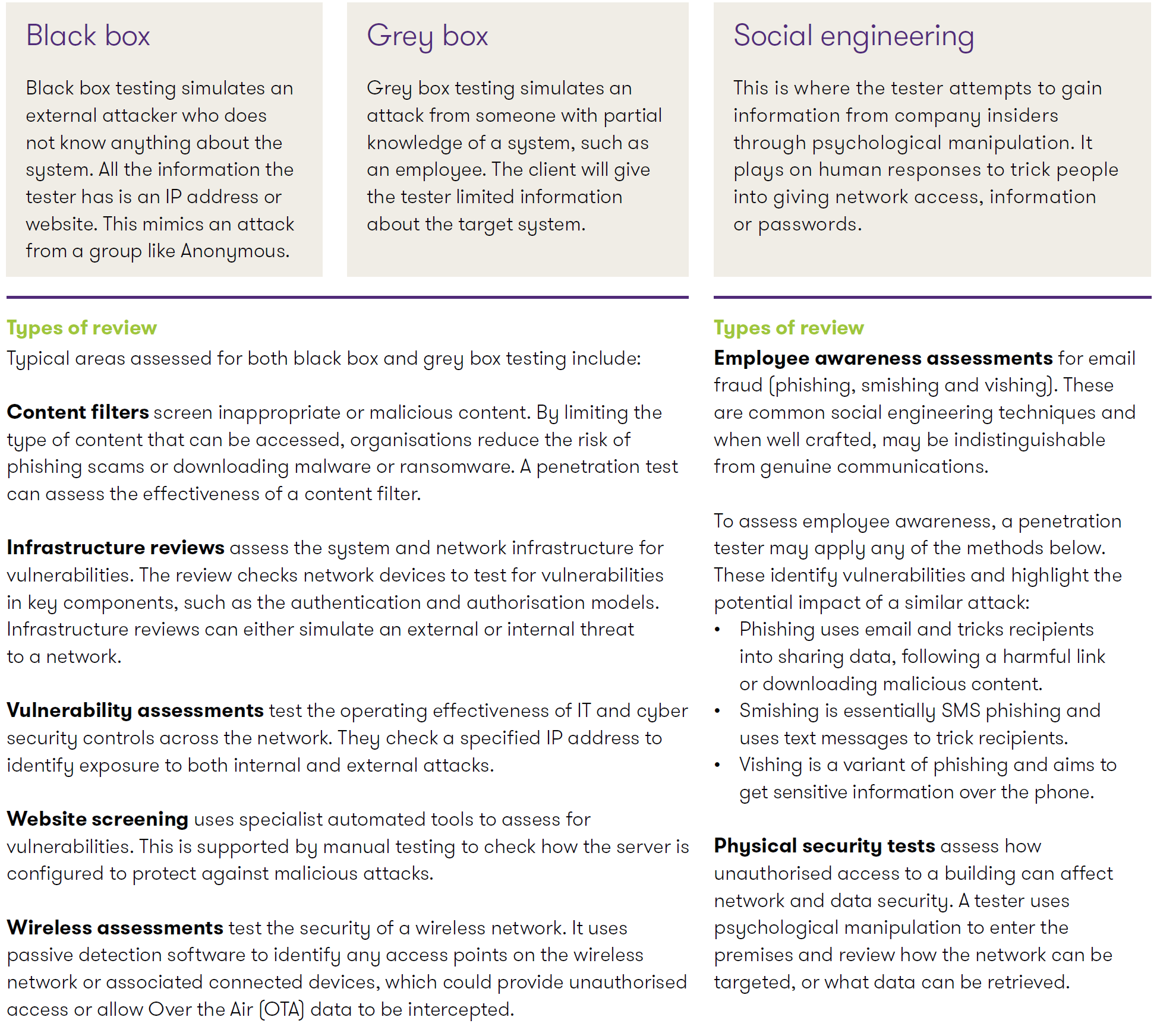
A penetration test essentially aims to gain unauthorised access to a network. It mimics what a person with a malicious motive would attempt to achieve. It applies a range of techniques, including social engineering, to breach an organisation’s security perimeter.
Approaches to penetration testing
Technology is not infallible and nor are people. An effective penetration test should assess network vulnerabilities from both the cyber standpoint and the human element. It should mirror different types of attack, based on the amount of information an attacker might have or their preferred technology.
How we can help
Our penetration tests assess how robust a cyber security system is in practice. They simulate common methods used by attackers, taking into account both the technical and human elements which make up the full security perimeter. We help organisations understand the full range of vulnerabilities and implement improved controls to mitigate those risks.
At Grant Thornton, our cyber security experts can develop a bespoke penetration testing plan to meet your business needs and unique IT environment. We can undertake the full suite of testing or conduct individual assessments, as required. Our experts can test for vulnerabilities around particular areas of concern, or help identify unforeseen issues across the network.
Our subject matter experts have significant experience in IT and cyber security, working with clients across all industries. The team can assist in the following areas:
- cyber security governance and strategy
- cyber security architecture
- firewall configuration and management reviews
- firewall rule-set reviews
- audits of security controls
- information security management reviews
- physical security reviews
- PCI-DSS reviews and audits
- training and awareness sessions for staff and senior management (eLearnings & classroom trainings)
Sophisticated cyber attacks pose a serious threat for organisations today. Many businesses, have had their data compromised due to insecure systems and a lack of safeguards. Data breaches can have serious financial and legal implications, as well as lasting reputational damage.